Review admin consent requests
In this article, you learn how to review and take action on admin consent requests. To review and act on consent requests, you must be designated as a reviewer. For more information, check out the Configure the admin consent workflow article. As a reviewer, you can view all admin consent requests but you can only act on those requests that were created after you were designated as a reviewer.
Prerequisites
To review and take action on admin consent requests, you need:
- An Azure account. Create an account for free.
- An administrator role or a designated reviewer with the appropriate role to review admin consent requests.
Review and take action on admin consent requests
Steps in this article might vary slightly based on the portal you start from.
To review the admin consent requests and take action:
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator who is a designated reviewer.
- Browse to Identity >Applications >Enterprise applications.
- Under Activity, select Admin consent requests.
- Select My Pending tab to view and act on the pending requests.
- Select the application that is being requested from the list.
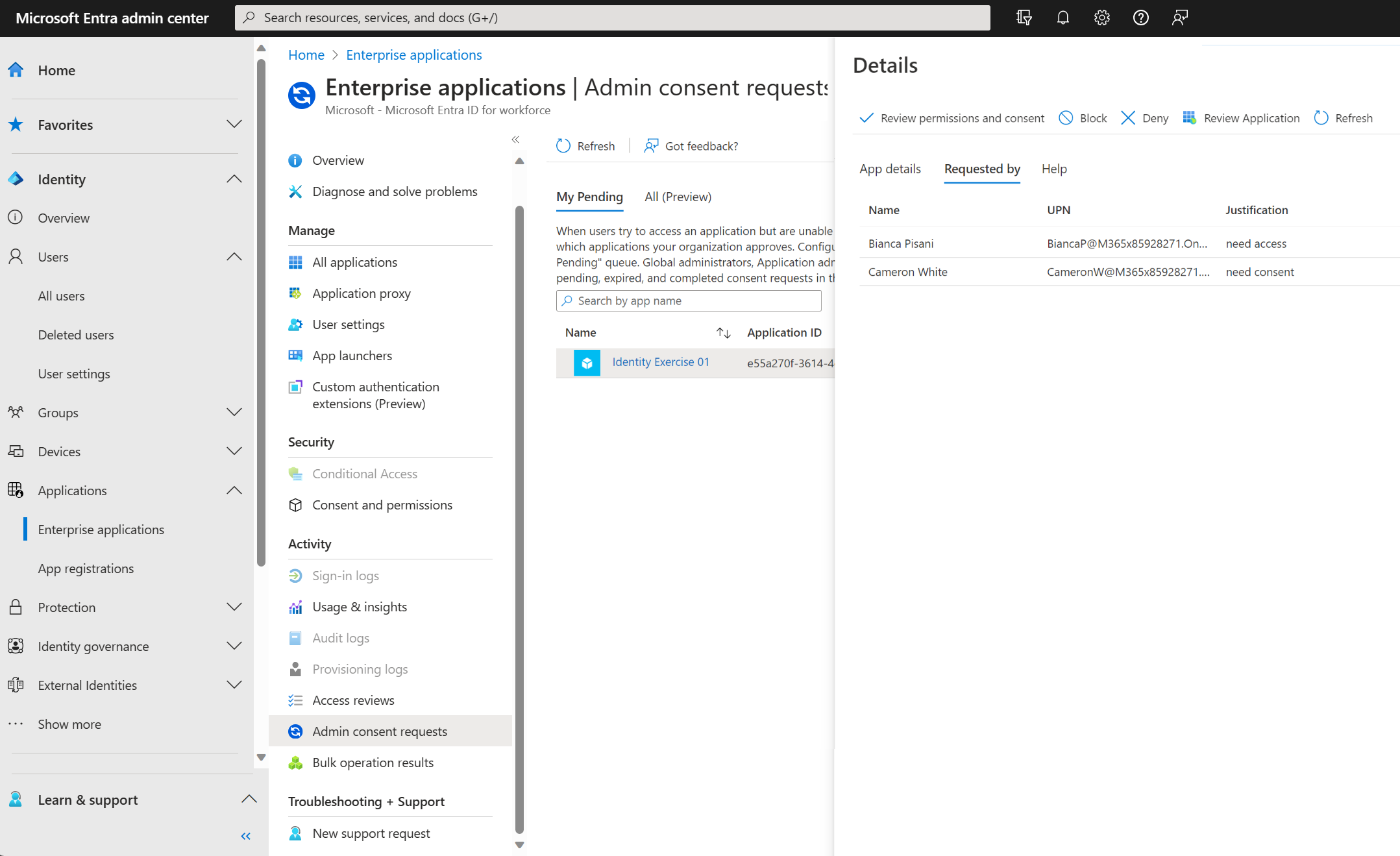
- Review details about the request:
- To see what permissions are being requested by the application, select Review permissions and consent.
- To view the application details, select the App details tab.
- To see who is requesting access and why, select the Requested by tab.
- Approve the request. To approve a request, grant admin consent to the application. Once a request is approved, all requestors are notified that their request for access is granted. Approving a request allows all users in your tenant to access the application unless otherwise restricted with user assignment.
- Deny the request. To deny a request, you must provide a justification that is provided to all requestors. Once a request is denied, all requestors are notified that their request for access is denied. Denying a request won't prevent users from requesting admin consent to the application again in the future.
- Block the request. To block a request, you must provide a justification that is provided to all requestors. Once a request is blocked, all requestors are notified that their request to access the application is denied. Blocking a request creates a service principal object for the application in your tenant in a disabled state. Users won't be able to request admin consent to the application in the future.
Review admin consent requests using Microsoft Graph
To review the admin consent requests programmatically, use the appConsentRequest resource type and userConsentRequest resource type and their associated methods in Microsoft Graph. You can't approve or deny consent requests using Microsoft Graph.
Next steps
- Review permissions granted to apps
- Grant tenant-wide admin consent


